Researchers found a set of 13 new vulnerabilities affecting the Nucleus TCP/IP stack, which we are collectively calling NUCLEUS:13. The new vulnerabilities allow for remote code execution, denial of service, and information leak.
Nucleus is currently owned by Siemens and it has been deployed in many industries that have safety and security requirements, such as medical devices, automotive and industrial systems.
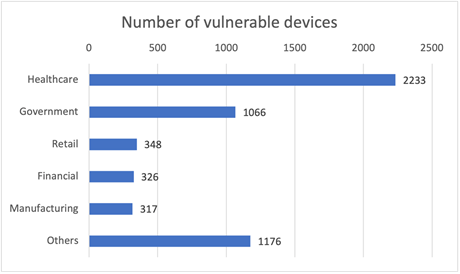
The most severe vulnerability (CVE-2021-31886 ) with CVSS3.1 score of 9.8 is a remote code execution that affects FTP server.
FTP server does not properly validate the length of the “USER” command, leading to stack-based buffer overflows. This may result in Denial-of-Service conditions and Remote Code Execution.
Please find the attached file for the complete list of CVEs
–RECOMMENDATIONS:
Complete protection against NUCLEUS:13 requires patching devices running the vulnerable versions of Nucleus. Siemens has released its official patches and device vendors using this software should provide their own updates to customers. Below are mitigation strategies for network operators:
· Discover and inventory devices running Nucleus. Forescout Research Labs has released an open-source script that uses active fingerprinting to detect devices running Nucleus. The script is updated constantly with new signatures to follow the latest development of our research.
· Enforce segmentation controls and proper network hygiene to mitigate the risk from vulnerable devices. Restrict external communication paths and isolate or contain vulnerable devices in zones as a mitigating control if they cannot be patched or until they can be patched.
· Monitor progressive patches released by affected device.
· Monitor all network traffic for malicious.
· The table below provides recommended mitigations for each vulnerability:
| CVE | Affected component | Mitigation Recommendation |
| 2021-31885 2021-31886 2021-31887 2021-31888 | FTP / TFTP server | Disable FTP/TFTP if not needed, or whitelist connections. |
| 2021-31881 2021-31882 2021-31883 2021-31884 | DHCP client | Use switch-based DHCP control mechanisms: protocol-aware network switches may be configured to block DHCP responses from rogue servers (“DHCP snooping”). Alternatively, firewalls can be configured in a similar fashion. As a last resort, use static IP addresses. |
| 2021-31344 2021-31345 2021-31346 2021-31889 2021-31890 | TCP / UDP / IP / ICMP | Monitor traffic for malformed packets and block them. Having a vulnerable device behind a properly configured firewall should be sufficient. |
–REFERENCES:
https://secure-web.cisco.com/1ENR_KMhV_DMJD27I6nyuZ_7-_j9nuDw4TC-8SAONQsUvJdafI-f4Um8i05C3cqcRLZGq8NfW6dU4CWx9uKFRbqdy7LFPMfQIjr83_vCelgILzOS-Mm5TOhMt64uPqvpa1Xf19hfgrOR7ryymaKaHZkjyAHIC6CdHgl-c3EYpXDTFPfVwVNXllVlzJGzFqHDOyfJZiflDgdM_kN9E6wKBe-6J8BQs3d69tTGABmnwl7g/https%3A%2F%2Fwww.forescout.com%2Fresources%2Fnucleus13-research-report-dissecting-the-nucleus-tcpip-stack%2F
https://secure-web.cisco.com/1iLUdNnPwsElvvqzbWSMO7q2GPOVmm3q8iIVoZHylPsEWGEtKwMIZdmWy06I-dMqsWv6U6aXl_i98wr_AToJOUV5YPYX1BXXCz5jP48bLatvLTy1PX9jAKRpW91Jdg3Q3_qzOGFGnQW51xRdhq2mb0OMLwgZIYG4gIx9-qEVfRqYXtkAzGll-6IWxciwEfdZKpDSMhvWl_LJnlezG5lUkF7-tLwE1pI77_oXTPbx5d-k/https%3A%2F%2Fus-cert.cisa.gov%2Fics%2Fadvisories%2Ficsa-21-313-03